Security - Attacks
There are two different types of attacks, passive attack and active attack.
Passive Attack
Attempt to learn or make use of information, but not affect system resources.
Such as, release message contents and traffic analysis.
It is relatively hard to detect, but easier to prevent by encryption.
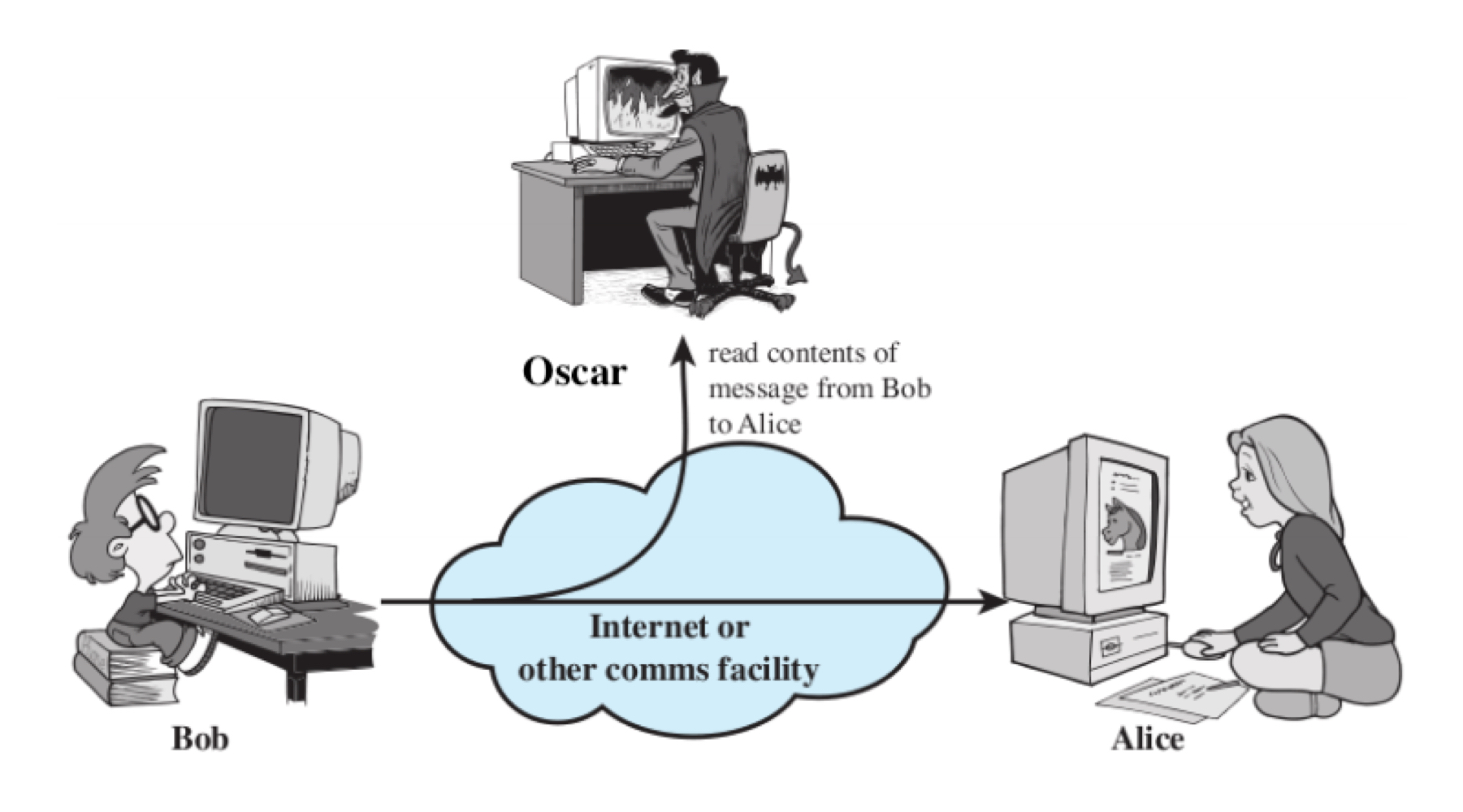
Realease Message Contents
Message content is one of the passive attack. It involves the intruder stealing all the message or data transmitted. The information gathered by the intruder is stolen unethically.
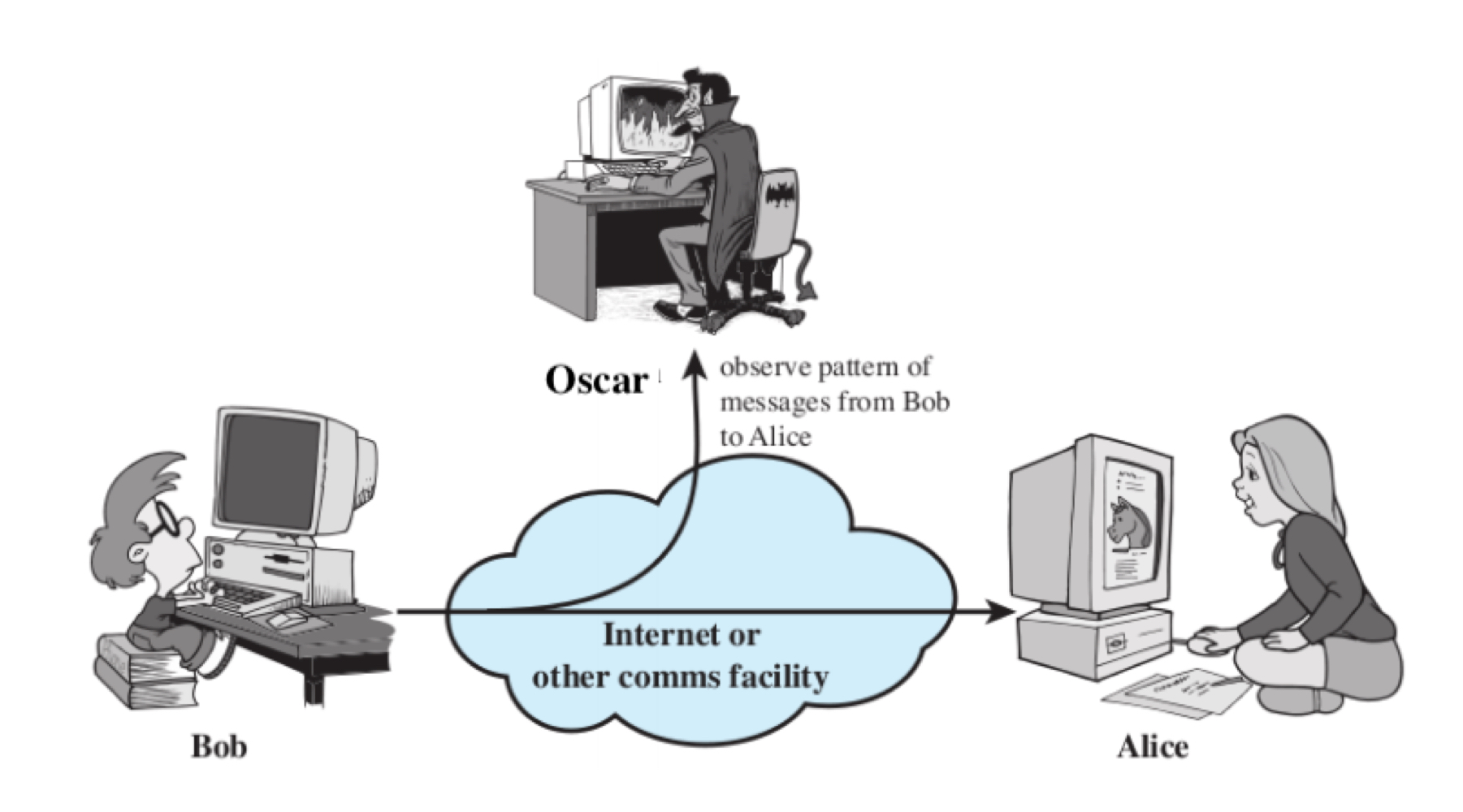
Traffic Analysis
Masked traffic analysis is also one of the passive attack. It involves messages or data eing encrypted before transmission. The message being masked the intruder can’t read the message but only understand the pattern and length of encryption.
Active Attack
Attempt to alter system resources or affect their operation.
It is relatively hard to prevent because it would require physical protection of all communications facilities and paths at all times, but easier to detect.
There are four categories.
- Maquerade
- Replay
- Modification of messages
- Denial of service
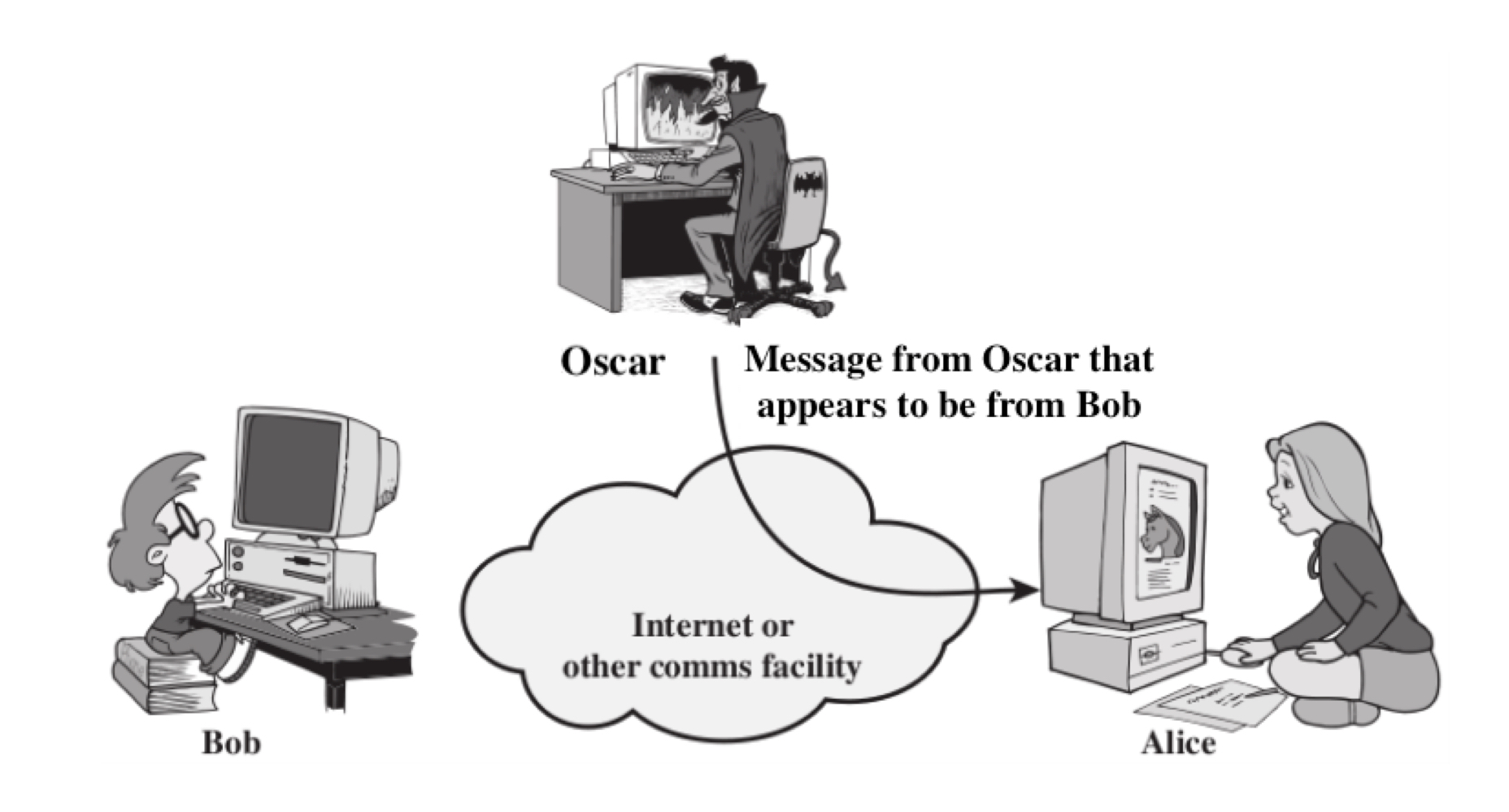
Masquerade Attack
The attacker tampers the information received by the receiver by claiming itself as the sender. It takes place when one entity pretends to be a different entity. It includes one of the other forms of active attack.
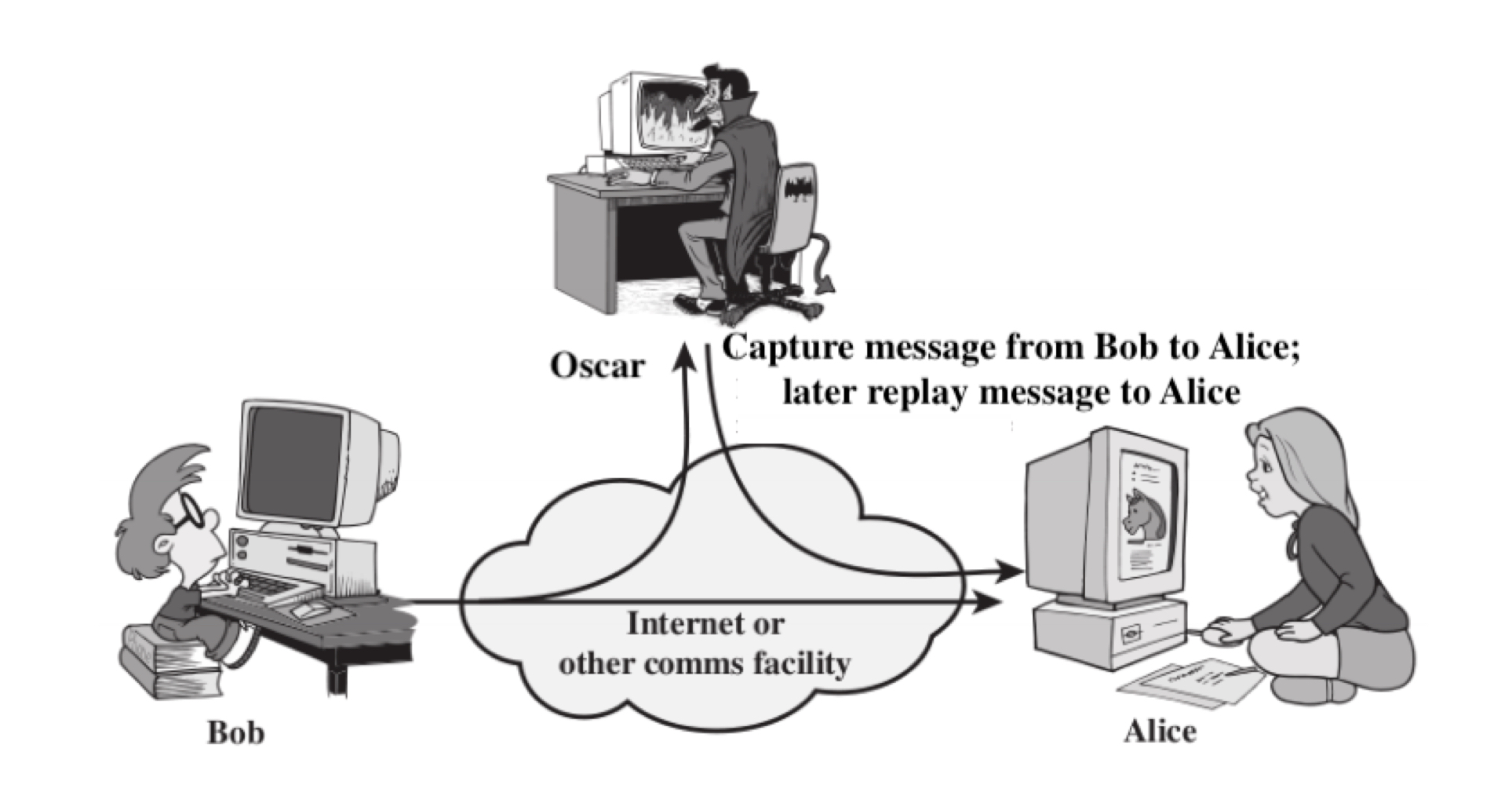
Replay Attack
The attacker attacks the transmitted message through a passive channel and make the final message received by the receiver may appear to be authorized and safe. It involves the passive capture of a previously transmitted message and replaying it to produce an unauthorized effect.
Modification Attack
Some portion of a legitimate message is altered, or messages are delayed or reordered to produce an unauthorized effect.
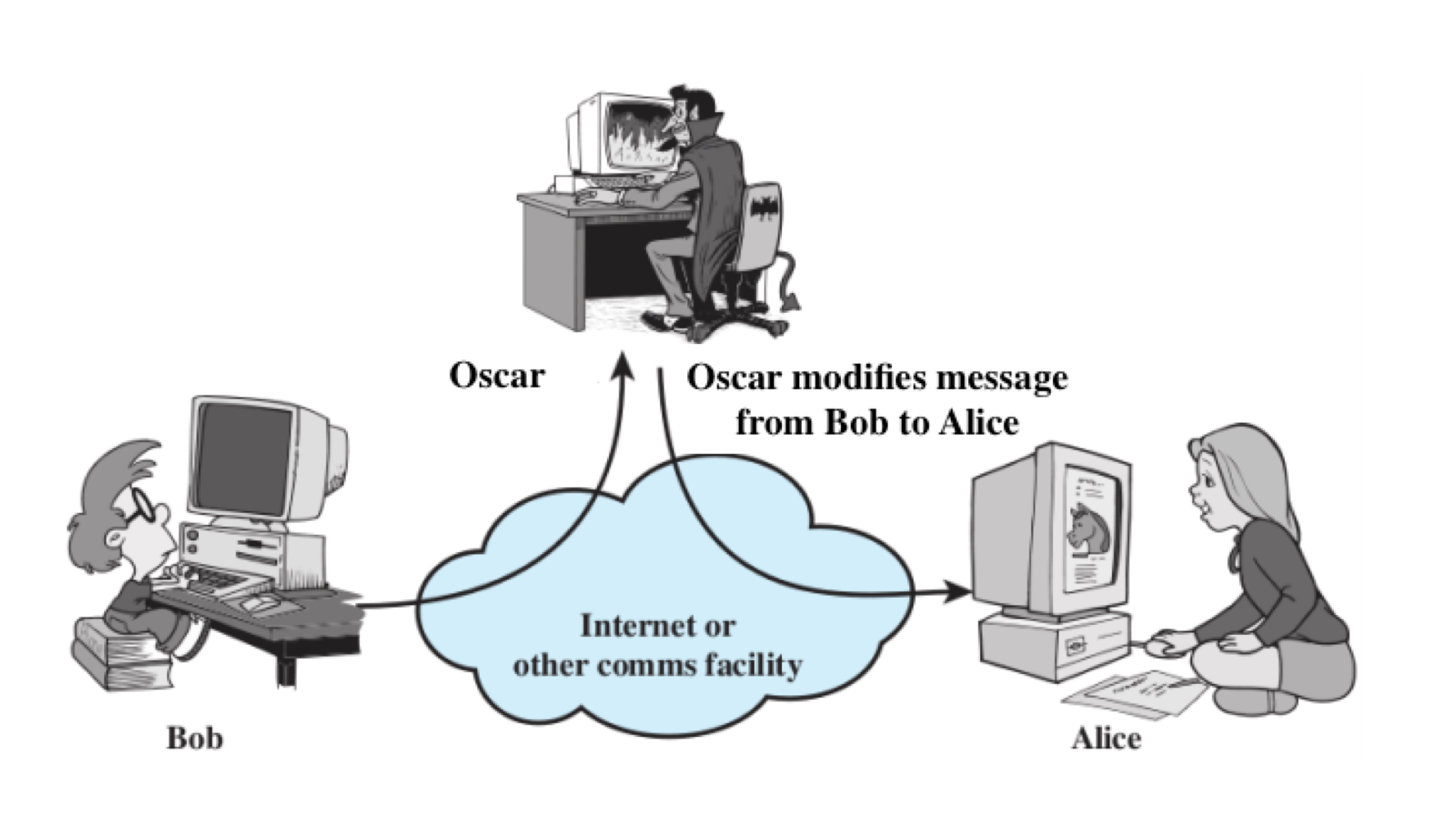
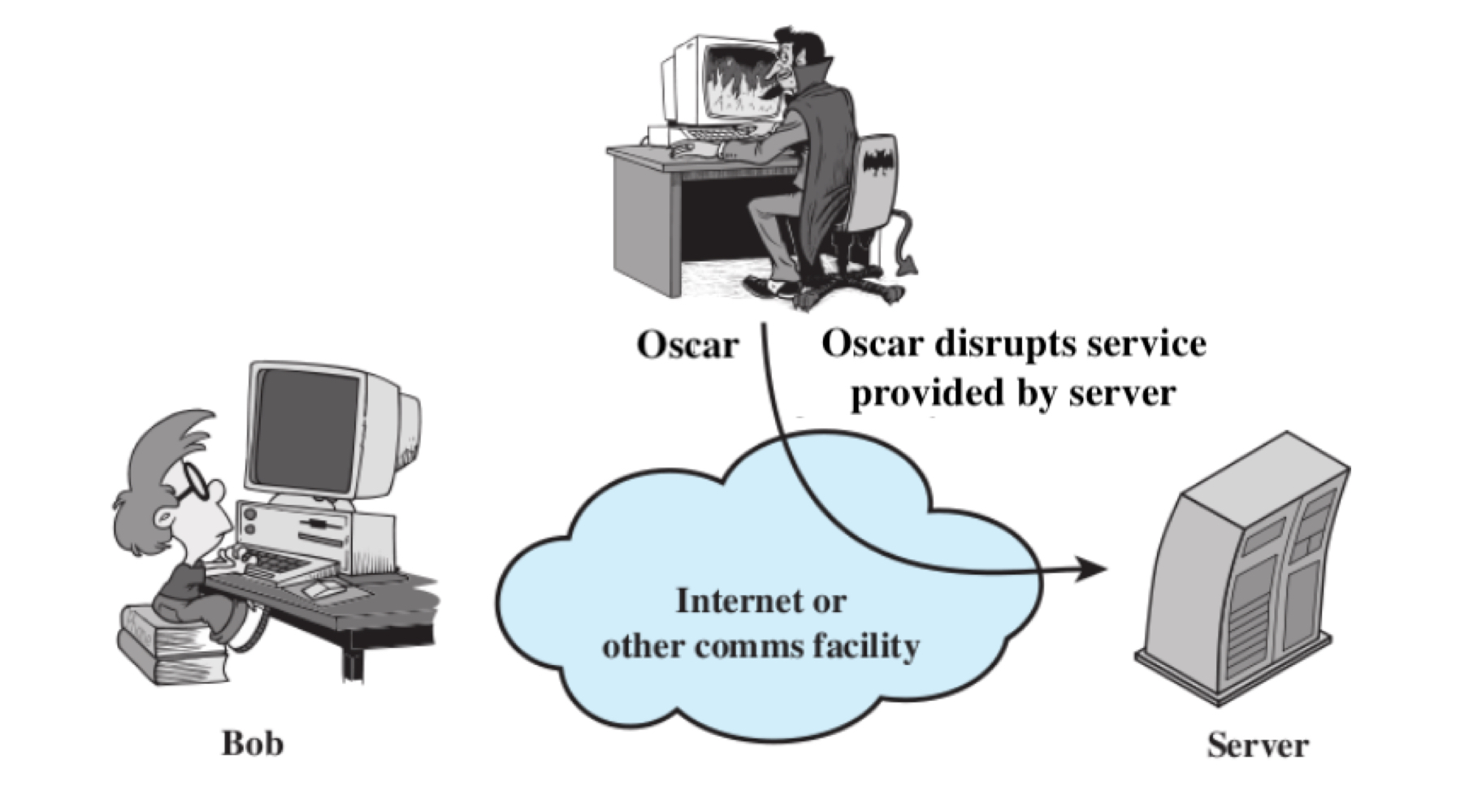
Denial of Service Attack
The receiver is prevented from receiving the transmitted message as there is an overflow of requests to the receiver, which makes the services hampered from their usual behavior.
Enjoy Reading This Article?
Here are some more articles you might like to read next: